Docker私有仓库
原创2023年7月17日大约 4 分钟
为了使用自己开发的阿里云解析而生。
同时解决无法登录及发布Docker Hub的问题。
包括SSL、基本认证、Docker Registry UI、删除镜像内容。
更多的配置可在Docker Resistry和Docker Resistry UI找到。
docker-compose.yml
第8行:Registry UI的域名SSL证书目录第9行: 自己的Nginx配置文件第13行: Registry的URL地址第29行: Registry的仓库存储目录第30行: Registry的域名SSL证书目录第31行: Registry的基本认证目录第33行: Registry允许跨域访问的地址
version: '3.8'
services:
registry-ui:
container_name: REGISTRY_UI
image: 'joxit/docker-registry-ui:2.5.2'
volumes:
- <SSL证书目录>:/etc/nginx/certs
- <nginx的conf.d配置目录>:/etc/nginx/conf.d/
ports:
- 443:443
environment:
- NGINX_PROXY_PASS_URL=<REGISTRY的URL>
- SHOW_CATALOG_NB_TAGS=false
- DELETE_IMAGES=true
- REGISTRY_TITLE=Neverland
- SINGLE_REGISTRY=true
- CATALOG_MIN_BRANCHES=1
- CATALOG_MAX_BRANCHES=1
- CATALOG_ELEMENTS_LIMIT=1000
- SHOW_CONTENT_DIGEST=true
- TAGLIST_PAGE_SIZE=100
depends_on:
- registry
registry:
container_name: REGISTRY
image: 'registry:2.8.2'
volumes:
- <Registry存储目录>:/var/lib/registry
- <Registry SSL证书目录>:/certs
- <Registry 用户认证目录>:/auth
environment:
- REGISTRY_HTTP_HEADERS_Access-Control-Allow-Origin=[<Docker Registry UI地址>]
- REGISTRY_HTTP_ADDR=0.0.0.0:443
- REGISTRY_HTTP_TLS_CERTIFICATE=/certs/docker.pem
- REGISTRY_HTTP_TLS_KEY=/certs/docker.key
- REGISTRY_AUTH=htpasswd
- REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm
- REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd
- REGISTRY_HTTP_HEADERS_Access-Control-Allow-Methods=['HEAD', 'GET', 'OPTIONS', 'DELETE']
- REGISTRY_HTTP_HEADERS_Access-Control-Allow-Credentials=['true']
- REGISTRY_HTTP_HEADERS_Access-Control-Expose-Headers=['Docker-Content-Digest']
- REGISTRY_STORAGE_DELETE_ENABLED=true
- REGISTRY_HTTP_HEADERS_Access-Control-Allow-Headers-Control-Allow-Headers=['Authorization', 'Accept', 'Cache-Control']
- REGISTRY_HTTP_HEADERS_X-Content-Type-Options=[nosniff]
- Access-Control-Max-Age=[1728000]
ports:
- 443:443Docker Registry
拉取Registry
docker pull registry:latest启动Registry
docker run -d \
--restart=always \
--name registry \
-p 5000:5000 \
registry:latest预览Registry
curl http://127.0.0.1:5000/v2/_catalog返回:
StatusCode : 200
StatusDescription : OK
Content : {"repositories":[]}
RawContent : HTTP/1.1 200 OK
Docker-Distribution-Api-Version: registry/2.0
X-Content-Type-Options: nosniff
Content-Length: 25
Content-Type: application/json; charset=utf-8
Date: ... GMT...
Forms : {}
Headers : {[Docker-Distribution-Api-Version, registry/2.0], [X-Content-Type-Options, nosniff], [Content-Length, 25], [Content-Type, application/json; charset=utf-8]...}
Images : {}
InputFields : {}
Links : {}
ParsedHtml : System.__ComObject
RawContentLength : 25修改配置(不安全)
打开daemon.json文件或者在Docker Desktop的Docker Engine添加如下配置,SSL无需此配置。
"insecure-registries": [
"http://127.0.0.1:5000"
],跨域
-e REGISTRY_HTTP_HEADERS_Access-Control-Allow-Origin="['*']"添加Docker Registry SSL
证书从服务提供商获取,示例
.crt证书大部分包含中间证书,所以这里用.pem来代替
docker run -d \
--restart=always \
--name registry \
-v "$(pwd)"/certs:/certs \
-e REGISTRY_HTTP_ADDR=0.0.0.0:443 \
-e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.pem \
-e REGISTRY_HTTP_TLS_KEY=/certs/domain.key \
-p 443:443 \
registry:2添加认证
提示
只用Docker界面配置时,可以将保存的用户密码文件auth目录挂载即可。
步骤按官网如下:
为用户创建一个密码文件,其中包含一个条目,密码:testusertestpassword
mkdir auth docker run \ --entrypoint htpasswd \ httpd:2 -Bbn testuser testpassword > auth/htpasswd在 Windows 上,请确保输出文件已正确编码:
docker run --rm --entrypoint htpasswd httpd:2 -Bbn testuser testpassword | Set-Content -Encoding ASCII auth/htpasswd停止注册表。
docker container stop registry使用基本身份验证启动注册表。
docker run -d \ -p 5000:5000 \ --restart=always \ --name registry \ -v "$(pwd)"/auth:/auth \ -e "REGISTRY_AUTH=htpasswd" \ -e "REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm" \ -e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd \ -v "$(pwd)"/certs:/certs \ -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt \ -e REGISTRY_HTTP_TLS_KEY=/certs/domain.key \ registry:2尝试从注册表中提取镜像,或将镜像推送到注册表。 这些命令失败。
登录到注册表。
docker login myregistrydomain.com:5000提供第一步中的用户名和密码。
测试您现在可以从注册表中提取镜像或将镜像推送到 注册表
Docker Registry UI
拉取Docker Registry UI
docker pull joxit/docker-registry-ui启动Docker Registry UI
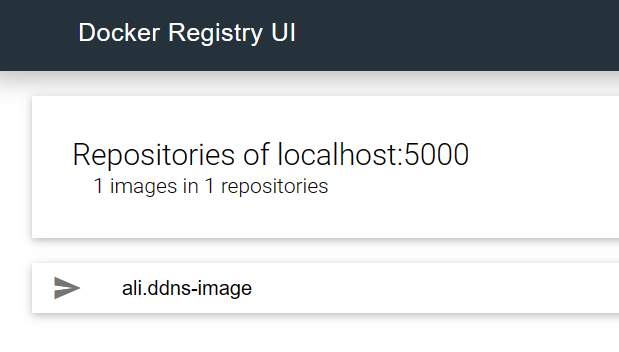
docker run -d -p 8080:80 -e REGISTRY_URL=http://localhost:5000 --name docker-registry-ui joxit/docker-registry-ui预览Docker Registry UI
浏览器输入http//localhost:8080
添加Docker Registry UI SSL
内部使用nginx代理,配置.conf文件即可,其中需要改动的地方以高亮显示。
5-6行:对应的证书位置
18行:对应Docker Registry 访问地址
26行:对应Docker Registry UI访问地址
server {
listen 443 ssl;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_certificate /etc/nginx/certs/fullchain.pem;
ssl_certificate_key /etc/nginx/certs/privkey.key;
root /usr/share/nginx/html;
# disable any limits to avoid HTTP 413 for large image uploads
client_max_body_size 0;
location /v2 {
# Do not allow connections from docker 1.5 and earlier
# docker pre-1.6.0 did not properly set the user agent on ping, catch "Go *" user agents
if ($http_user_agent ~ "^(docker\/1\.(3|4|5(.[0-9]-dev))|Go ).*$" ) {
return 404;
}
proxy_pass http://registry:5000;
}
}
server {
listen 80;
location / {
# Force HTTPS
return 301 https://$host$request_uri;
}
}上传镜像
标记镜像
docker tag ali.ddns-image 127.0.0.1:5000/ali.ddns-image:v1推送镜像
Docker push,将本地镜像推送到registry仓库中
docker push 127.0.0.1:5000/ali.ddns-image:v1拉取镜像
删除本地已有镜像,从私有仓库拉取
docker pull 127.0.0.1:5000/ali.ddns-image:v1Docker Registry
curl http://127.0.0.1:5000/v2/_catalog返回:
StatusCode : 200
StatusDescription : OK
Content : {"repositories":["ali.ddns-image"]}
RawContent : HTTP/1.1 200 OK
Docker-Distribution-Api-Version: registry/2.0
X-Content-Type-Options: nosniff
Content-Length: 25
Content-Type: application/json; charset=utf-8
Date: ... GMT...
Forms : {}
Headers : {[Docker-Distribution-Api-Version, registry/2.0], [X-Content-Type-Options, nosniff], [Content-Length, 25], [Content-Type, application/json; charset=utf-8]...}
Images : {}
InputFields : {}
Links : {}
ParsedHtml : System.__ComObject
RawContentLength : 25Docker-Registry-UI
浏览器输入http//localhost:8080